Despite the US making cannabis regulations challenging to navigate, the industry is snowballing toward profitability. New Jersey legalized adult use cannabis on April 21 this year. One month earlier, The Garden State began accepting applications for Class 5: Retailers, Dispensing and Delivery.
Although New Jersey isn’t shy about its licensing requirements and standards, many people want to know how retailers can stay in the game for the long run. So, let’s talk about risk management considerations New Jersey retailers need to know.
Top Risks Cannabis Retailers Face in New Jersey
Regardless of what kind of retailer you operate —medical or adult use — it’s critical to know what you’re up against. The following are the most common risks we’ve watched cannabis retailers face daily in New Jersey, making a customized risk management strategy necessary.
Theft
Like other retailers, New Jersey cannabis retailers are vulnerable to theft. Unfortunately, theft can come from various angles, such as in-store, in-transit and insider crime. Besides cannabis retailers typically having a well-stocked inventory, it’s not uncommon for them to have more cash on hand than most other businesses.
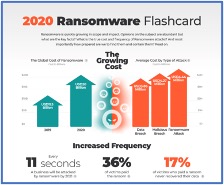
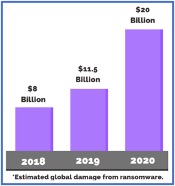
Although the SAFE Banking Act could positively impact the cannabis industry, it’s in a notorious stall yet again. Briefly, the SAFE Banking Act would no longer allow financial institutions, such as banks and credit card companies, to refuse to do business with cannabis companies. However, cannabis retailers must operate in a cash-only environment, for now, forcing them to make bank runs multiple times a day. We probably don’t have to explain how enticing a significant inventory and fat bank bags look to criminals.
Cybersecurity
 Since the onset of the global health crisis, the cyber liability landscape has nearly spun into a death spiral. In other words, cybercriminals sat on the edge of their seats during the pandemic, waiting to pounce on anything that looked slightly vulnerable. Remote workers, small businesses, and emerging industries were hard-hit.
Since the onset of the global health crisis, the cyber liability landscape has nearly spun into a death spiral. In other words, cybercriminals sat on the edge of their seats during the pandemic, waiting to pounce on anything that looked slightly vulnerable. Remote workers, small businesses, and emerging industries were hard-hit.
It’s no surprise that New Jersey cannabis retailers face many cybersecurity risks through their point of sale (POS) systems. Additionally, retailers often gather and store personal information, such as email addresses, credit card numbers, shipping addresses, etc. Hackers and cybercriminals gravitate to this vital data rapidly.
Property Damage
In addition to the risk of theft, as mentioned above, cannabis retailers must protect their property from losses. Without adequate protection, damage to equipment or buildings could add up to high out-of-pocket costs. Consider the damage a weekend office fire or late-night vandalism would cause. If property damage occurs, retailers must figure out how to sustain business operations while recovering from the loss simultaneously. As a result, New Jersey retailers must protect their property and maintain business continuity.
How to Customize a Risk Management Strategy
Watch or listen to any news reports and there’s a decent chance that you’ll feel some slight sense of doom and gloom. And sure, a lot is going wrong in our world; however, that doesn’t need to impact how you perceive your businesses. Instead of casting a massive net over every possible risk that you can imagine, we recommend trying the following 5-step approach. Here’s the gist:
- Identify: Pinpoint high-level risks that are specific to the cannabis industry. Then, let the process trickle down to focus on company-specific exposures.
- Analyze: Determine how badly a particular risk could harm your retail company. How much will this hurt should the “what-ifs” play out?
- Evaluate: Categorize risks according to how risk tolerant your company is. Will you avoid, transfer, mitigate or accept the risk?
- Track: Use your history or the stats from a similar retailer to map out how you’ve handled the risk over time. Older retailers have an advantage over younger retailers, of course, but you can still get a feel for your risk management style.
- Treat: Make good on your evaluation promises by avoiding, transferring, mitigating, or accepting the various risks you identified.
Recommended Insurance for New Jersey Retailers
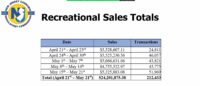
The New Jersey Cannabis Regulatory Commission issued detailed requirements for new cannabis businesses. That said, part of the application requirements considered is the plan for companies to obtain liability insurance. Many new retailers opted for a “letter of commitment” as opposed to a certificate of insurance (COI), stating their plans for obtaining the following coverages:
- Commercial general liability: Protects cannabis companies against basic business risks.
- Product liability: Protects against claims alleging your product or service caused injury or damage.
- Property: Reimburses cannabis companies for direct property losses.
- Workers’ compensation: Covers employees if they are injured on the job and can no longer work.
In addition to the required insurance coverages, we recommend New Jersey retailers customize their risk management package with these policies:
- Crime: Protects your cannabis company against specific money theft crimes.
- Cyber: Protects your cannabis company against damages from specific electronic activities.
- Directors & officers: Protects corporate directors’ and officers’ personal assets if they are sued.
- Employment practices liability: Protects cannabis companies against employment-related lawsuits.
- Professional liability: Protects cannabis companies against lawsuits of inferior work or service.
With more states in the US entering the marketplace soon, New Jersey is doing its fair share of the heavy lifting by spearheading the onboarding process. Remember, doing your due diligence at the start pays off in the long run — New Jersey retailers are proving that. Consider teaming with a commercial insurance broker calibrated to the cannabis industry, so you get the most out of your broker, marketplace and the cannabis industry as a whole.